Dominion Voting Systems is the leading provider of election computers to America’s swing states (Georgia, Wisconsin, Michigan, Pennsylvania, Arizona). They therefore get a lot of attention from conspiracy-theorists.
The latest is a claim that Dominion’s “EMS” servers have a backdoor password of “dvscorp08!”, hardcoded in every server they’ve sold for over a decade.
The fact are (probably, uncontroversially) true. The characterization is not.
Dominion’s cyberscurity rests upon preventing physical access to the machines, keeping them air gapped from the Internet.
Anyone with physical access to the machines can subvert them, with or without backdoor passwords. Every scenario shown above can already be done without those backdoor passwords.
Even if you fixed that problem, Dominion has a bunch of other holes. In other words, Dominion is going to fix this by using Windows operating-system accounts instead of MS-SQL accounts, but this is just a band-aid that doesn’t actually change the security of the system. The password hashes will just be Windows password hashes instead of MS-SQL password hashes.
The ultimate fix is to re-architect things from scratch, using such technologies as TPMs and DPAPI, to make the security architecture work more like how your phone works, where somebody with physical access can’t subvert the security. But this only marginally improves security — hostile election workers would still be able to subvert elections.
Details
It’s incredibly irritating that these people don’t actually go into details about what the heck they are talking about.
Consider Supreme Court decisions: they go in detail explaining every step to the point that even non-lawyers can understand. It’s tedious as heck, but you can read the exact reasoning the justices used to come to the decision.
These conspiracy-theorists do the opposite, skipping steps and important information such that even experts aren’t certain what, precisely, is going on. We have to make educated guess about what they might mean. This process is deliberate — they are creating an argument to entice those with little knowledge of the system, not building a case that can withstand skeptical experts.
Simply saying “backdoor password” doesn’t tell us what’s going on. The first question is “for what?”. The three common contexts are:
BIOS passwords
Windows account passwords
Database passwords
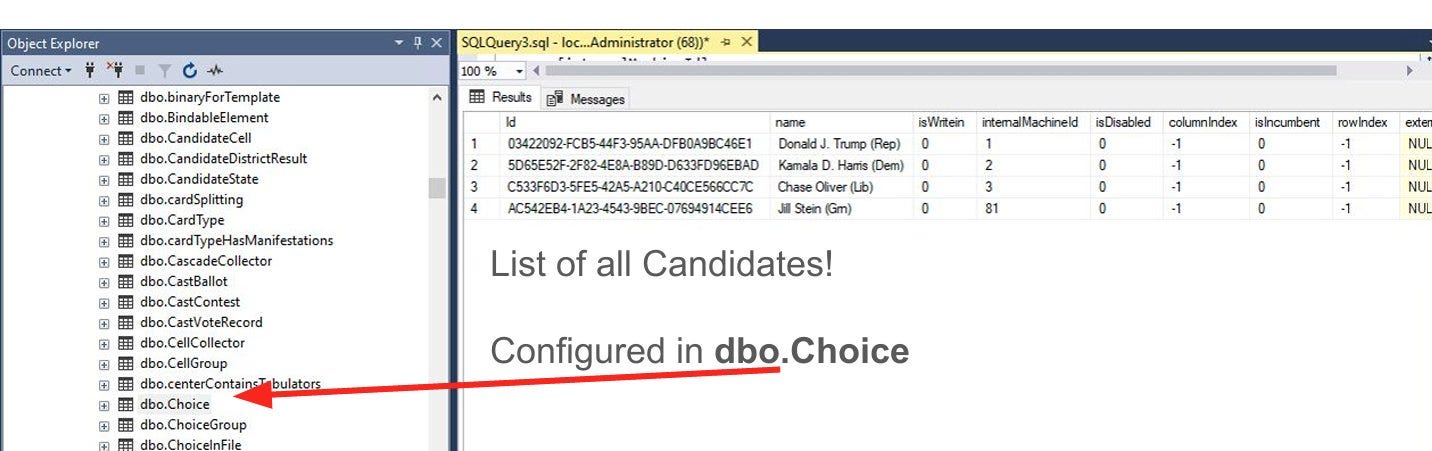
In this case, “dvscorp08!” is the password for the a database (MS-SQL) account named “SAdmin”, on the “Dominion EMS” server. This is an administrative account that has full control over the database, meaning it can change values (like the number of votes) and even change some code called “stored procedure calls” that return different totals of votes, without changing the votes themselves.
The problem with Dominion’s EMS server is that it doesn’t really have security against hostile insiders. If you have physical access to the machine, you can already do such things as change votes and source code. The reason is that if you were a hostile insider, you could subvert the election in other ways, without needing to do the hacks described here.
Dominion EMS server
The system in question is Dominion’s “Election Management System” or “EMS”.
This is the central component of Dominion’s “Democracy Suite” of products which includes a lot of other things, such as ballot marking devices (BMDs) and tabulators.
Each county runs their own election, and will have one EMS, usually locked away in a room. The EMS is air gapped from the Internet, though will usually be part of a small local network connected to other devices.
The larger the county, the more the components of EMS will be split among various servers and workstations on the air gapped network. For a small county, like Mesa County in Colorado, most components are located on a single server.
The system manages many stages of the election, such as shown in the graphic:
Elections are much more complex than you think. In your mind, you simply get a paper ballot, mark which President you want, it then gets counted, and that’s the result.
But in America, we typically overload the Presidential election with all the other races. It’ll usually contain state elections, such as your local legislature representative. It’s also contain local county offices, like the water commissioner. It may contain municipal elections, like the local mayor.
The following is a ballot image from Douglas County in Georgia form 2020:
The races that can change throughout the county are the U.S Representative, the State Senator, the State Representative, and the Education District.
So before the election, a worker sits down to use the Dominion “Election Event Designer” app to design all these apps. This can include such tasks as creating audio files for use in ballot marking devices to help those with vision problems. It’s a lot of work.
Among the lack of details is where this dbo.Choice stored procedure comes from. It comes from the Designer app that designs the next election event. It’ll eventually be used after the election during Tallying of results. To really understand this, we need a full description of how all this works. Note that the screenshot in the thread only lists the Presidential race, not any of the numerous other races happening at the same time. I’m not sure if this is real information of an actual race — there’s no information where the hacker got this.
During and after the election comes the “tabulation” of votes. Dominion’s devices are called “ImageCast”, because among the things they do is to record an image of the ballot (such as the image above) before counting the votes. These devices can be connected via the air gapped network to the EMS, or more often, they record everything to a flash drive, which is then manually transported to the EMS and read in.
A worker then uses a “Results Tally and Reporting” app to then collect and report the votes.
Services
The EMS is built using standard modern technologies. In this case, they use the technology suite from Microsoft. The web server is running IIS server-side components written in C# that most then access the separate MS-SQL database. “IIS” is the name of Microsoft’s web server that comes with Windows, “C#” is the programming language most often used to write these components, and “MS-SQL” is Microsoft’s database software.
The specific problem here is hardcoded passwords in the C# code and within the database. This is common practice, because such servers are physically isolated from the world, but it’s not best practice.
It’s common because one component needs to connect to another, and that requires an account. Code running within the web server needs to log into the database just like any other user.
The Microsoft solution is “integrated” accounts, so that instead of the MS-SQL server maintaining it’s own login accounts (like “SAdmin” using the “dvscorp08!” password, that it instead trusts a Windows account.
In other words, Windows maintains a list of login accounts to log into Windows, and the database maintains login accounts to log into the database, and these are separate. But they don’t have to be: you can tell the database to trust Windows. You’ll still see something like “SAdmin” here in the database, but instead of password, you’ll see which Windows account that maps to.
It’s much like how a lot of websites allow you to login using your Apple, Google, or Facebook credentials without having to create a password specially for that website.
Security
To fix Dominion’s security would be to rearchitect the system to work more like an iPhone, where any “hard coded passwords” are stored in a tamper-proof chip.
Dominion’s security rests upon physical access, preventing outsiders from accessing the machines. Their machines, or local networks, are air gapped from the rest of the Internet, so hackers can’t get in. There is little to no protection against hostile insiders, as we’ve seen in Mesa County (Colorado) and Coffee County (Georgia), where Republican election officials allowed conspiracy-theorists to access the machines after the 2020 election.
The point is that getting rid of these machines will not secure elections. Malicious election workers can already subvert the elections without the machines.
Having computers tabulate ballots is certainly a problem because people don’t trust computers, but the reality is that if we got rid of computers and hand-counted all elections, reliability and trustworthiness of the elections would go down, not up.
Now with computers, we do have the opportunity to improve security and also guard against hostile insiders, but this would require a complete redesign of Dominion’s architecture.
But the security improvements would be small. You still have to trust administrators. All that you’d be doing is securing the system against hostile election workers.
How to do with without a backdoor password
The disk is not encrypted. Somebody could access the disk physically and change all this. (You can’t meaningfully encrypt the disk without a hardware TPM chip like what you have in your phone).
Anybody who can login to access the server, such as uploading votes to tally, can execute database commands to change values in the database. That’s what they are doing when uploading new votes. This can be done at any workstation with any user account.
All these things can be subverted outside of the EMS before sending the data to be tallied.
Without computers, ballots can be tampered with using the same techniques they could always have been tampered with. There are a lot of security controls to make this harder, but dedicated malicious elections workers can still cause problems.
How to discover such a hack
Among many other things, the timestamps would change. The hack shown here changing the stored procedure would be trivially detected.
After an election, the entire database is archived and can be audited to discover such things.
Conclusion
Details matter. The post above doesn’t contain enough details for experts to really know what’s going on. It only lists suggestive things, hoping to convince non-experts.
I try to go into more details in this post, but it would really require an entire textbook to explain it all.
In short, the scenarios described don’t need this “backdoor password”. It’s relying on the fact that people are scared by the concept of a “backdoor password”.
Dominion has crap security. It’s really only designed to keep outsiders out, and doesn’t do a good job protecting against malicious insiders. But malicious insiders have plenty of opportunity to subvert the system even without touching Dominion’s servers.
Sure, Dominion is going to “patch” this problem, but it’s not a real fix. The real fix is to redesign the security from scratch, such as using TPMs to encrypt the hard-drive.




Thanks. I always got mad at the people who claim elections are only secure if we use paper. The term "stuffing the ballot box" has non-metaphorical origins.