The Wire, Xcheck, and DKIM
A version of the email can be made public, to be verified, without compromising their source.
Out of India is a story about Facebook malfeasance, namely a claim that Facebook gives Indian politicians the ability to censor content. Facebook denies the allegations, and claims some of the proof on Indian news site “The Wire” was fabricated. The Wire then published a Facebook internal email that seems to confirm the veracity of their original reports. Facebook claims that email was also fabricated, but The Wire claims they verified the email with “DKIM”. There’s more discussion of the controversy here.
I’m a well-known expert on DKIM verification, so I thought I’d write up some notes.
The point of this post is there’s no reason The Wire can’t release a redacted-but-verifiable copy of the email. They can strip off the envelope identifying the recipient, but leave the content still verifiable with DKIM. The content doesn’t identify the recipient — meaning, it doesn’t identify the “whistleblower”, the “source” of the story.
DKIM is a modern extension to email servers that “signs” outgoing messages using cryptography. This prevents spam and phishing attacks from “spoofing” the sender of messages. Incoming messages are verified as truly coming from the sender they claim.
An accidental side effect is that when emails are leaked, they can be verified as authentic — that they haven’t been changed or fabricated. This was the case with the Hunter Biden emails copied from his laptop. Even if we couldn’t verify the rest of the laptop contents, we could verify some of the emails.
Back when the Hunter Biden laptop story broke, I called foul, criticizing the journalists for not DKIM authenticating the emails. They then sent me their “smoking gun” email, which I reluctantly verified as being true — in a way that anybody can replicate my work. DKIM can validate such emails even when we distrust the source of them. It’s the magic of cryptography.
In the current story, there is good reason to believe the email has been fabricated. The picture shows the email from The Wire’s story.
The interesting bit is the text at the end that includes the phrase “post which”, meaning “after which”. This is common phrasing in Indian English, but nearly unheard of in American English (that spoken by Andy Stone). It’s strongly suggestive of chicanery.
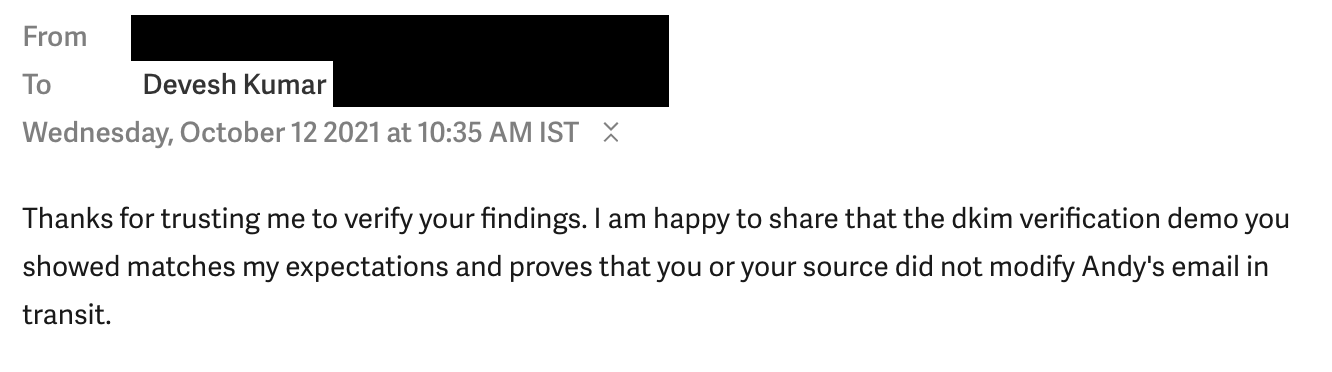
There is another problem. The Wires cites two “experts” who have validated the email with DKIM. They show an email from one of these anonymous experts, which people quickly noticed has a year of 2021 instead of 2022:
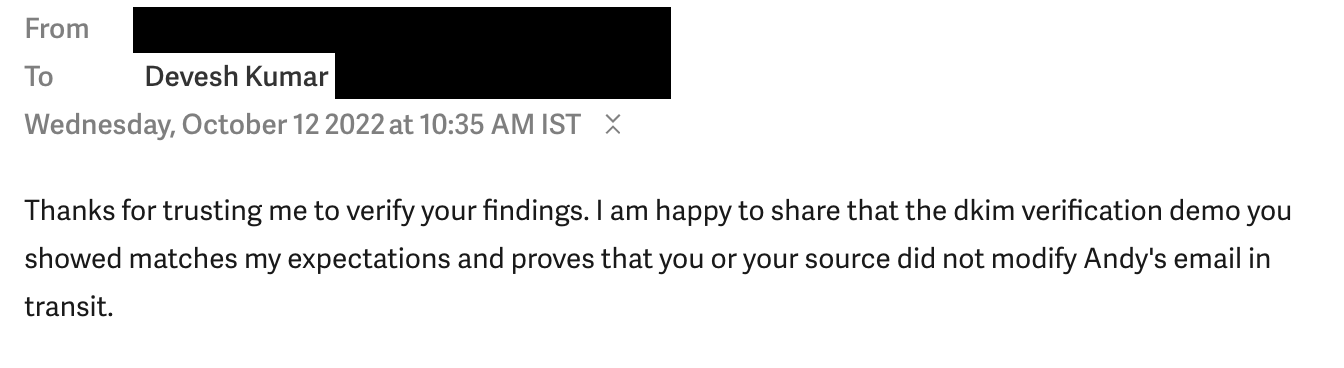
After critics point this out, the image was changed in the story with the correct date of 2022:
The Wire claims the fault was with “Tails” misconfigured with the wrong date. “Tails” is a self-contained operating-system (based on Linux) that can run from a USB drive, often used by activists and journalists for the dark web, to preserve privacy. The Wire claims they fixed the date and took new screenshots to fix the problem.
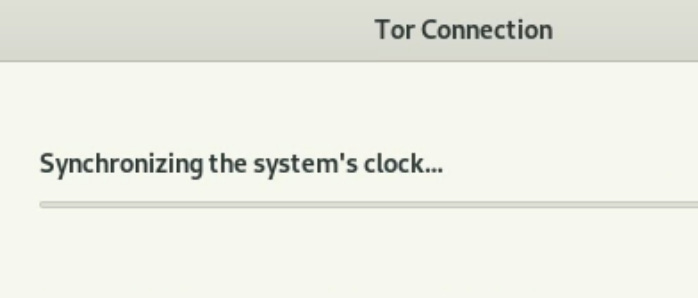
This doesn’t make sense. For one thing, it’s not the way Tails works — the first thing it does is synchronize clocks.
For another thing, this isn’t how a misconfigured date would work, it would affect outgoing emails, not the display of incoming emails.
For yet another thing, they obvious didn’t take new screenshots, but photoshopped the old one, as proven by the lack of space between the ‘2’ and the ‘a’.
Moreover, there is as bizarre problem with the dates. October 12th falls on a Wednesday in 2022, but on a Tuesday in 2021. This weirdly implies that the original screenshot is in error, not the redacted screenshot.
I used Tails to access ProtonMail and deliberately set the clock backwards, as shown in the screenshot below. You can see how the wrong date doesn’t change the display of received emails, and how there is space after the number ‘2’.
It’s unclear what’s precisely going on here, but it’s clear some sort of shenanigans are afoot. It’s not absolute proof, as I don’t know precisely which email system they are using, but it’s clearly off.
But this post is really about DKIM, the technology that’ll confirm the original message. The Wire claims that it can’t provide the original email because it would identify their source. This is true — the original, unaltered message file could do so.
However, they can still provide a redacted version — one that will pass DKIM verification, but which won’t contain the metadata that identifies their source.
The reason is because there are two types of metadata in an email message: metadata about the envelope and metadata about the contents.
Validation of the contents doesn’t require the envelope. Stripping the envelope doesn’t change the contents of the message inside.
With the Hunter Biden email that I validated two years ago, I show two versions of the message, the original, and a modified one with the envelope stripped off. Both pass verification, because the contents aren’t modified, only the envelope.
The Wire can do something similar. It would look something like the following:
They’ve already showed us all this in their video, which is why I (well, actually somebody else) can reconstruct almost all of it.
If The Wire has the expertise to use DKIM to validate an email message, they should easily have the expertise to strip out any privacy-invading envelope headers.
The point of this is that The Wire is needlessly withholding the email. They can redact identifying information of their source, namely, the envelope data identifying the person to whom it was sent, and provide us the rest of the message.
Being able to validate the message would increase our faith in it, but there’s still reason for doubt. DKIM verification would only prove it was sent through those servers. This is useful for something like GMail, where two people not employed by Google use the service. But when somebody is an insider, they have opportunity to use the infrastructure in ways outsiders don’t. Facebook insiders have a high likelihood of being able to spoof the sender’s email address in ways that GMail outsiders would not.
The conclusion is this: either the source or the journalists at The Wire are being dishonest somewhere. It doesn’t mean that the story is wrong, but gives us good reason to doubt it.
If they want to send me the message, in a form that can be validated (meaning, with envelope data stripped out), I’ll happily confirm the DKIM signature. This would help restore some of the reputation of the journalists.
Updates:
The Wire has temporarily pulled the story and is investigating. The main author of the story has removed his Twitter account. The measure of an organization like The Wire isn’t whether they make mistakes like this, it happens to the best of news organizations. The measure is how they respond.


The above source claiming DKIM verification has disavowed it.